A passwordless future, how would that work?
Passwords can be the weakest link for any business. It takes just one compromised password to bring an entire organisation to its knees. Passwords can be shared, forgotten, hacked, or stolen.
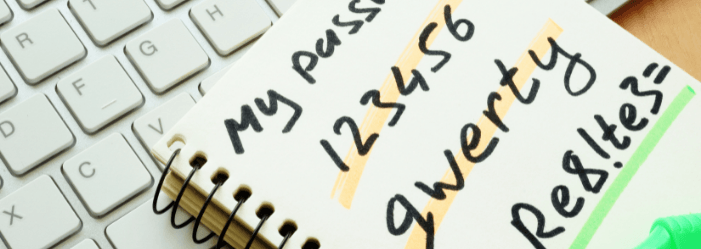
The introduction of passwordless logins can decrease the chances of a potential hack.
Here's what users should know about passwordless logins, how they work, and why they're considered much safer than the traditional way of accessing online accounts.
Passwordless Logins: What Are They?
Passwordless logins (Also known as multi-factor authentication MFA) use alternative authentication methods to allow users access. Sometimes, passwordless logins are combined with the use of keys for doubled security.
The use of passwordless logins is safer. Passwordless logins might also turn out to be easier for the end-user, requiring nothing complicated to remember.
Methods like two-way authentication, one-time-password use and fingerprint or biometric tracking are some of the methods used.
Financial institutions and high-security companies were the first to switch to these methods of authentication. If you want to protect the safety of your web users, you should too.
Superior to Passwords
Current methods of password authentication require the combination of a username and password. Let's be honest: it's weak, with most people proven to use passwords that are simple to guess. I'm looking at you Qwerty and Pa55word.
It's far too common for users to use the same password across several platforms. For companies, it presents a cyber security nightmare. These details are easy to forget, share, or steal. That's a risk most companies (and personal users!) would prefer to avoid.
Password managers can increase risk instead of reducing it, with one stolen password putting an entire company at risk. If you do away with passwords entirely, you also negate many of the cyber security risks they might pose to your company.
The consensus is that passwordless logins are the way to a better, more secure future.
A Stronger Stronghold
Passwords are an unnecessary risk when better options are available.
Phishing, ransomware and forgetfulness can sink a business by attacking just one password. Since many employees will use the same password across multiple sites, other hacks can even backfire and affect your business and security.
Passwordless authentication is the direction your business needs to be heading in.
Unpacking Passwordless Authentication
There's one thing that all methods of passwordless authentication have in common: authenticating the user by means other than the traditional (and tedious) username and password.
• OTPS: One-time-Pin authentication methods provide the user with a passkey through a verified device. The OTP is usually temporary and will expire within minutes to hours of being requested.
• BIOMETRICS: Biometrics authentication systems use visual tracking to identify and authenticate the user. This is becoming an increasingly popular choice for high-security systems: proper biometrics systems are harder to fool.
• PUSH Notifications: Push notifications authenticate the user via an app, combined with a platform login. It works much like an OTP system but through a separate system instead of a simple code.
• Fingerprints: Fingerprint systems require a physical fingerprint (and sometimes heat signature) to authenticate the user.
Good For Business
In new research published by NordPass an average person has more passwords than an average pop song has words. As the digital age continues, the list of passwords to remember will only increase.
Don't risk your entire business on the strength of user passwords: switch to superior
multi-factor authentication methods today.
Click here to learn more about the cyber security options available for your business, or
click this link to speak to a cyber security expert today.